Introducing AAI
Students want simple and secure access to web resources they need for their study, also to the ones located outside the university they are enrolled at.
Administrators of web resources want to provide secure access to users entitled to use their resource, with as low overhead as possible.
That is where AAI is strong at! AAI, the Authentication and Authorization Infrastructure, supports easy and secure inter-organizational access to web applications.
Let’s see what AAI can provide to you.
Without an AAI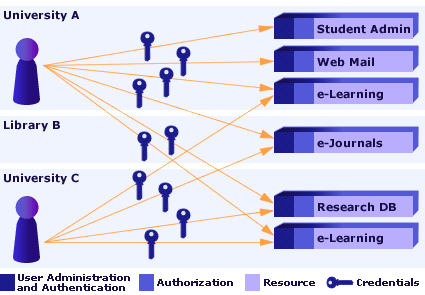
Without an AAI, a user registers with each Resource he/she wants to access and usually gets for each Resource a new username and password pair, so-called credentials. The problems are obvious:
- Users have to deal with too many username and passwords, typically one pair for each Resource.
- Each Resource administrator has to register the users on his/her own.
With an AAI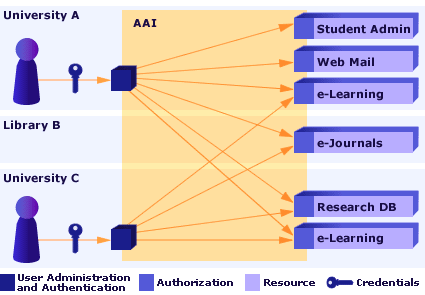
The AAI simplifies the processes for all parties involved using the concept of federated identity management:
- A user registers only once – namely with his/her so-called home organization to which the user is affiliated.
This Home Organization is responsible for maintaining the user related information and provides the user with the credentials. Home Organizations can be institutions like universities, libraries, university hospitals etc. - Authentication is always carried out by the user’s Home Organization, which can also provide additional information about the user to the Resource upon Resource’s request and user’s consent.
Like this, all AAI-enabled Resources are available to a user with a single set of credentials. At the same time, there is no need for Resource operators to register new users, because they get the required information directly from the user’s Home Organization. - An access control decision is made by the Resource based on the retrieved information about the user.
Thus federated identity management is based on the concept that Resources rely on user authentication at the user’s Home Organization and they obtain from there some information about the user for its authorization decisions.
KIF uses this federated approach to guarantee that each party remains in control of the steps relevant to it:
- Home Organizations register and authenticate their members
- Resource administrators define their access rules
KIF, on the other hand, operates the central AAI components and supports both Home Organizations and Resources.
Questions Regarding AAI?
Do you have any kind of questions regarding AAI? Please contact the KIF support(at)kif.kg.